Cybercrimes set new records year on year, with some research indicating that cybercrime increased by up to 600% due to the COVID-19 pandemic. Further jaw-dropping figures estimate that worldwide the global cost of cybercrimes is hovering around $6 trillion per year and estimated to have a global cost of US$10.5 trillion annually by 2025.
The figures may not have a direct impact on your business today, so it is tempting to scroll-on and focus on more pressing business priorities. The myth that IT-security is commonly considered an expensive, yet low business value line item in the company strategy may also not be aiding the correct decision-making process. Consider the following before scrolling on, the Australian Cyber Security Centre (ACSC) issued a notice to Australian organisations to adopt an enhanced cyber security posture and according to latest statistics, ransomware is 57-times more destructive in 2021 than it was in 2015.
The destructive nature of attacks should have gotten your attention, however the myth that IT-security is expensive is not necessarily true when operating in the Cloud. There are several simple and cost-effective approaches to assess and implement in order to protect your business workloads and decrease the attack surface of your cloud presence.
A simple, yet effective approach in enhancing your organisations cybersecurity posture is by having a plan – this goes without saying, however security due to urgency often results in a scattergun approach with teams implementing random security fixes, without considering the critical focus areas. Starting today with an immediate, yet practical plan improves effectiveness and decreases the chances of a scattergun approach during a suspected attack.
So where do we start with the practical security posture improvement plan? Some focus areas to consider:
- Define a phased approach, starting at a “stage 1” and set a period of approximately 60-days to deliver priority improvements. This approach keeps the outcomes real and delivers thread prevention results with business value.
- Be flexible yet focused on the critical threats and your business-critical workloads.
- Establish visibility across your AWS ecosystem – however remaining practical, starting on just your production account is a start.
- Focus on improving perimeter or edge security first.
- Infrastructure as Code (or automation) bring major benefits to the table, however, do not fall in the trap of delaying activities for months to improve security due to a lack of automation resources, or a lack of skills. Many of the critical security fixes and configurations targeted during the first 60-days, may only require once-off or infrequent configuration changes. Remain practical in the implementation methods chosen.
In this post, we will focus primarily on establishing practical visibility to guide your cybersecurity posture enhancement journey.
Applying our practical security posture plan to your workloads running in an Amazon Web Services ecosystem starts with awareness – establishing visibility. Several commercial options exist to address our visibility requirement; however, our focus will remain practical and cost-effective and with a lens to suit most organisations.
Amazon Web Services offer capable and informative services to provide cloud security posture visibility, including cost optimisation tips and much more.
A base level of security awareness is provided by AWS Trusted Advisor. Trusted Advisor offers insights across most workload components, including IAM-credential age, unrestricted security groups, and problem S3-bucket permissions, which till this day remains a common data breach access point. AWS Basic Support offers some visibility across critical areas, however subscribing to AWS Business or Enterprise Support offers the full suite of Trusted Advisor checks. The full suite of Trusted Advisor checks provides a well-established start to a practical cyber security posture enhancement.
Should you not subscribe to AWS Business or Enterprise Support, or simply need a focused lens on your security posture, AWS Config offers expanded visibility and provides an efficient console-based based remediation actions experience.
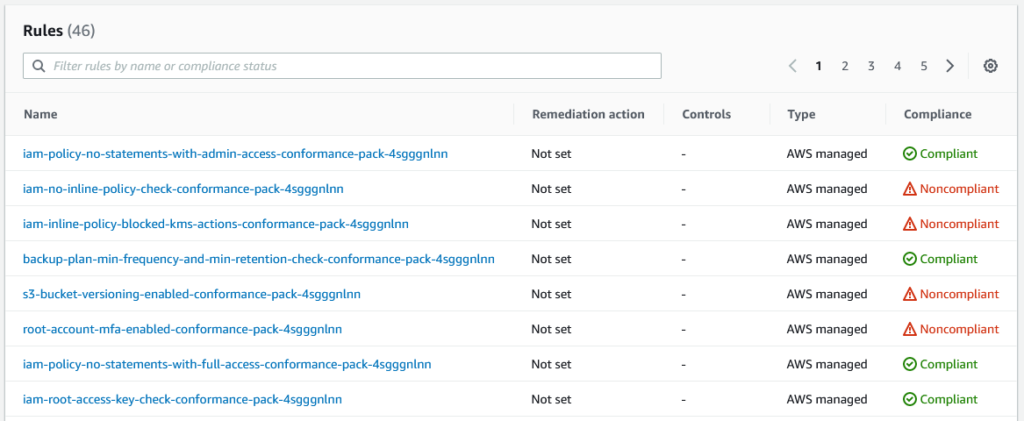
An effective start to AWS Config is by deploying one or more conformance packs. Conformance packs are pre-packaged sets of configuration rules covering operational best practice across various compliance requirements or other industry best-practice recommendations. The following conformance packs are recommended to kick-off security awareness:
- Operational Best Practices for AWS Well Architected Security Pillar
- Operational Best Practices for ACSC Essential 8
Various other conformance packs exist to address most compliance or operational insights, however starting with a focused subset will yield the most effective implementation to our practical security posture improvement plan.
AWS Security Hub should also be considered as an alternative and improved security posture service instead of AWS Config, as the integrations and insights offered by AWS Security Hub reach much further that AWS Config. AWS Security Hub makes use of AWS Config behind the scenes and aggregates the AWS Config findings into AWS Security Hub. Thus, the question is not necessarily the one versus the other, but rather what should be enabled on each of the services.
AWS Security Hub provides three major compliance and security standards, which may yield overwhelming results when turned on for the first time. As of 2022, these standards lenses are:
- AWS Foundational Security Best Practices v1.0.0
- CIS AWS Foundations Benchmark v1.2.0
- PCI DSS v3.2.1
A practical approach to start your cybersecurity posture enhancement visibility step is by following the a few simple steps:
- Enable AWS Config in all AWS regions
- Deploy the relevant AWS Config Conformance Packs – as noted above, start small, but focused
- Enable cross-region and cross-account aggregation for AWS Config. The approach taken here will depend on your specific needs or AWS account ecosystem
- Enable AWS Security Hub, however for your initial 60-days practical approach, do not enable any AWS Security Hub standards yet
- Enable at minimum the following integrations on AWS Security Hub: AWS: Config, Amazon: GuardDuty, AWS: IAM Access Analyzer, AWS: Health
- Enable AWS Security Hub cross-region aggregation
A major benefit of enabling and making use of AWS Security Hub is that security findings across most AWS services are aggregated into a single pane of glass for improved visibility and speedy action.
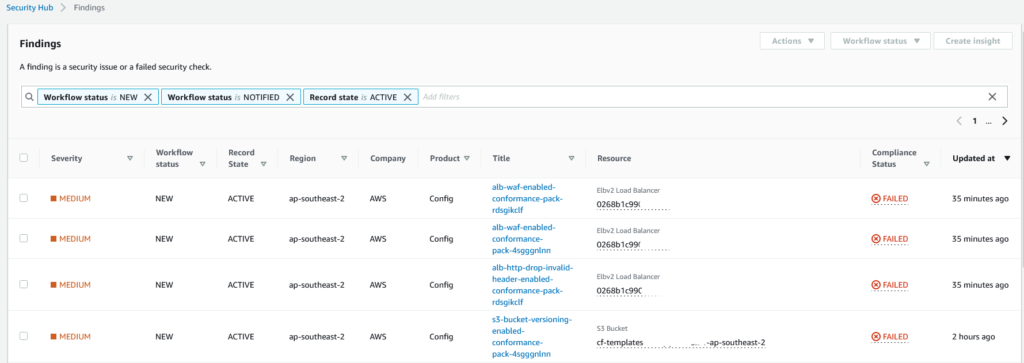
In addition, AWS Security Hub standards offer a scorecard-based approach to track your security posture enhancement efforts.
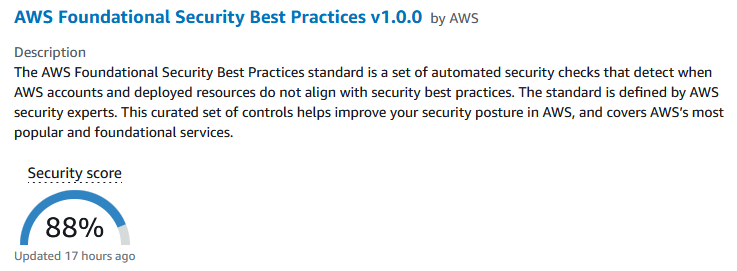
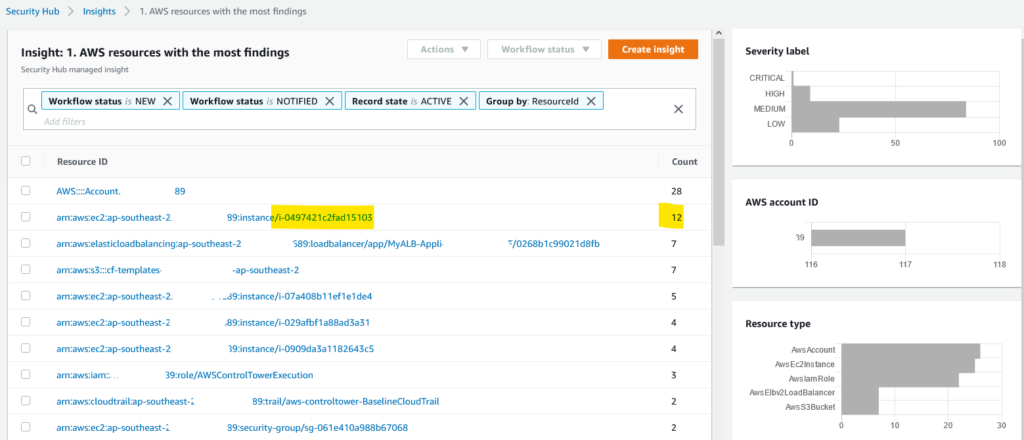
AWS Security Hub also offer insights across various findings out-of-the-box (findings patterns) to focus remediation attention. As showcased below, one insight pattern within AWS Security Hub highlights resources with the most findings – any easy way to focus on problem workloads or engineering teams.
Both AWS Security Hub and AWS Config is priced based on the volume of findings or configuration changes assessed. A simple yardstick may be around 0.5% to 1.0% of your AWS invoice, however, could be less.
It is considered best-practice to always enable AWS Config in all regions and configure the recorder to track all resources. This will provide you with a point-in-time snapshot of any changes made to AWS resources in the event of malicious or mistaken configuration changes. As it is a consumption-based service, you only pay for what you use (or in this case, what changes in your environment).
Following the initial round of security assessments and remediations, it is recommended to turn on additional conformance packs or enable AWS Security Hub standards applicable to your environment to build on the success and further improve your security posture.
This post focus on your AWS platform and workload security, however, it is important to note that the biggest threat to malware attacks remain internal staff with elevated network or system access. Issuing users with a secondary system identity/account for administrative purposes offer extra protection on the internal network. In addition, establishing a continuous security awareness program for all staff offer the best protection against malware attacks. Prevention is better than paying an expensive cybersecurity attack ransom.
Refer to the follow up post on a practical approach to improve your perimeter security following the establishment of your cloud security posture visibility.
For reference, additional statistics on cybercrime can be explored here.